First of all, NFC stands for Near Field Communication. It is a technology for wireless transfer of data between two devices. If that sounds a lot like BlueTooth or WiFi, that is because it is a similar.
NFC has its roots in RFID or Radio Frequency Identification. RFID tags are like bar-codes that don’t need to be scanned, but merely placed near an RFID reader. An RFID chip—which by the way can be smaller than a grain of rice—can be read by an RFID reader without the need for contact, so if a shopping mall were to tag everything via RFID, all a shopper would have to do is pass their shopping bag / trolley near an RFID reader, and all the products could automatically billed.
An RFID tag is essentially a chip storing some data which gets activated by an RFID reader. The radio waves from the RFID reader are intercepted by the RFID tag, and these are enough to power the device. The tag uses the power it gets from the RFID reader to send back its own radio message with the data it stores—or it could just have a small battery. In this case an RFID reader is a passive device that sends the same bits of data it is stored no matter what.
What if you were to create a similar system where two devices could communicate using similar means? Where both devices could work as both a tag and a reader to pass along small messages. Well, NFC is exactly such a system. NFC is in fact compatible with RFID, and you could have NFC tags, just like RFID tags.
Many experts say NFC really is fundamentally secure by virtue of its extremely short range. In order to snag your NFC signal, a hacker would need to be very close to you. Uncomfortably close. In other words, you’d know they were there. And unless it was a very intimate friend of yours, you’d likely not be happy about it.
|
Aspect |
NFC |
Bluetooth |
Bluetooth Low Energy |
|
RFID compatible |
ISO 18000-3 | active | active |
|
Standardisation body |
ISO/IEC | Bluetooth SIG | Bluetooth SIG |
|
Network Standard |
ISO 13157 etc. | IEEE 802.15.1 | IEEE 802.15.1 |
|
Network Type |
Point-to-point | WPAN | WPAN |
|
Cryptography |
not with RFID | available | available |
|
Range |
< 0.2 m | ~100 m (class 1) | ~50 m |
|
Frequency |
13.56 MHz | 2.4–2.5 GHz | 2.4–2.5 GHz |
|
Bit rate |
424 kbit/s | 2.1 Mbit/s | ~1.0 Mbit/s |
|
Set-up time |
< 0.1 s | < 6 s | < 0.006 s |
|
Power consumption |
< 15mA (read) | varies with class | < 15 mA (read and transmit) |
NFC technology is mainly aimed to be used in mobile phones. NFC uses both write and read technology. The connection is established when two NFC devices are bought within the distance of 4 centimeters.
Applications
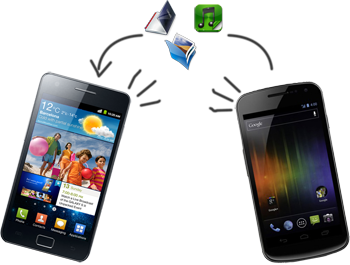
As you can guess from the name, and from its ancestry NFC is for communication between devices placed very close by, distances much closer than those required by BlueTooth or WiFi. In fact devices usually have to be touching or placed a few centimetres apart. While this might seem like a disadvantage, and most certainly can be in many situations, it also has its positive sides. While BlueTooth and WiFi require that a device be paired, or share a mutual password, NFC has no such requirements.
Authentication is assumed based on the fact that the devices are nearly touching, which would require both device users to choose to do so. In fact NFC can be used as an alternative to entering long WiFi keys or traditional means of pairing devices using BlueTooth. For example if you have a WiFi point that supports NFC, it could automatically transmit the WiFi key to any device that is placed very near it. Or, rather that start a tedious BlueTooth pairing process, you could simply tap two phones together and they would use that gesture as consent for a BlueTooth pairing. This particular feature is in fact available in Android in the form of Android Beam. While NFC can be used for data transfer, it can be quite slow for large amounts of data, especially when compared to BlueTooth or WiFi.
So Android Beam uses NFC and take advantage of its convenience in quick communication over short distances, and uses that to authenticate the devices so that that it can use quicker technologies for the actual transfer of data. As such it can transfer anything, music, videos, or the state of an application, such as tabs open in a browser, the saved state of a game etc. NFC is also finding many uses in places where RFID was used earlier.
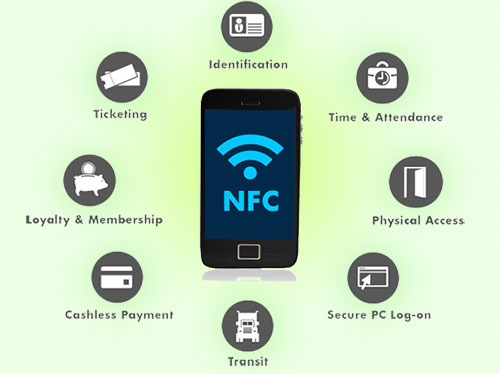
NFC isn’t a newfangled technology, but it’s just now beginning to filter into mainstream products like smartphones. With an NFC chip and antenna, you can use your smartphone to make contactless payments at NFC retail terminals, parking meters, taxis and many other places.
Key Benefits of NFC
NFC provides a range of benefits to consumers and businesses, such as:
- Intuitive: NFC interactions require no more than a simple touch
- Versatile: NFC is ideally suited to the broadest range of industries, environments, and uses
- Open and standards-based: The underlying layers of NFC technology follow universally implemented ISO, ECMA, and ETSI standards
- Technology-enabling: NFC facilitates fast and simple setup of wireless technologies, such as Bluetooth, Wi-Fi, etc.)
- Inherently secure: NFC transmissions are short range (from a touch to a few centimeters)
- Interoperable: NFC works with existing contactless card technologies
- Security-ready: NFC has built-in capabilities to support secure applications
For example it can be used as an alternative to ID cards. One up and coming use is as a means of payment. Google Wallet for example allows one to initiate payments by simply tapping your phone on a payment device. Your financial details can be stored on Google Wallet, and when you initiate a transfer using NFC, Google Wallet only needs your authorization for payment, and handles the rest. Games can use NFC to initiate a multiplayer gaming session and use WiFi or BlueTooth for the actual game data. Tapping mobile and tablets, or putting them in close proximity makes a lot of sense, but one is likely to have a hard time imagining such a thing working with desktops. Even so, a laptop or desktop fitted with NFC can use that functionality to enable all kinds of useful interactions. You could for example, transfer your browsing session to your tablet / mobile from your laptop / desktop before leaving home. Or sync between you laptop / desktop and mobile / tablet just by using NFC.
NFC is only one technology, with Bluetooth and RFID just as able to strike-up a conversation between two gadgets, but there are distinctions within NFC, too. In comes in both passive and active flavours, including P2P mode (exchanging information, such as business cards or contacts) and SecureElement NFC (where a machine recognises a NFC phone as a bankcard).
You won’t find NFC on many laptops or desktops but it is only a matter of time. Look at how BlueTooth is now common on any laptops and you will see how it is likely to find future laptops fitted with NFC. Desktops usually have neither but are flexible enough to use dongles to add those capabilities. There are tons of imaginative uses for NFC that people have yet to come up with. All one needs to know are the advantages of NFC at your disposal, quick initiation of communication, moderately fast data transfer speeds (around 400 kbit/s) and the possibility of having passive (without battery) items that interact with NFC devices.