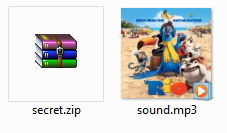
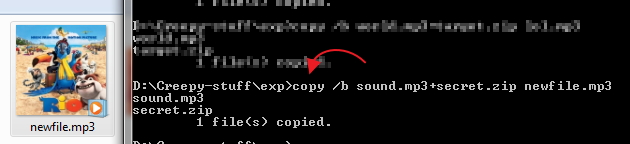
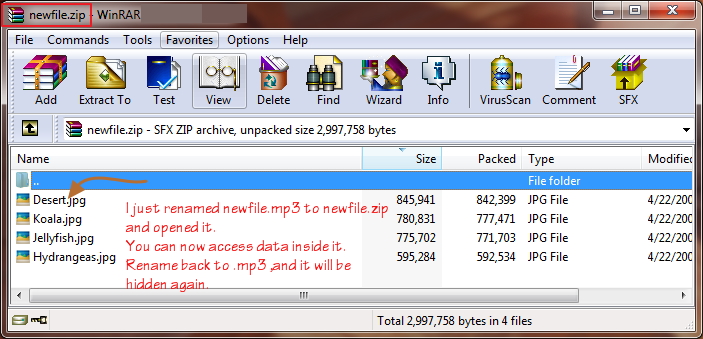
If you wanna remove those nasty ads from the pages which waste lot of time and bandwidth then here is something for you I believe will help you a lot. This is done without using any software.
It’s possible to set up a name server as authoritative for any domain you choose, allowing you to specify the DNS records for that domain. You can also configure most computers to be sort of mini-nameservers for themselves, so that they check their own DNS records before asking a nameserver. Either way, you get to say what hostname points to what IP address. If you haven’t guessed already, the way you block ads it to provide bogus information about the domains we don’t want to see – i.e., all those servers out there that dedicate their existence to spewing out banner ads.
Probably the most common way people block ads like this is with something called the “hosts file”. The hosts file is a simple list of hostnames and their corresponding IP addresses, which your computer looks at every time you try and contact a previously unknown hostname. If it finds an entry for the computer you’re trying to reach, it sets the IP address for that computer to be whatever’s in the hosts file.
127.0.0.1 is a special IP address which, to a computer, always means that computer. Any time a machine sends a network request to 127.0.0.1, it is talking to itself. This is very useful when it comes to blocking ads, because all we have to do is specify the IP address of any ad server to be 127.0.0.1. And to do that, all we have to do is edit the hosts file. What will happen then is something like this:
1. You visit a web page
2. The web page contains a banner ad stored on the server “ads.example.com”
3. Your computer says “ads.example.com? never heard of it. wait a second, let’s see if I’ve got the number on me…”
4. Your computer finds its hosts file and checks to see if ads.example.com is listed
5. It finds the hostname, which points to 127.0.0.1
6. “Great”, says the computer, and sends off a request to 127.0.0.1 for the banner ad that’s supposed to be on the page
7. “oh”, says the computer, and fails to show anything because it just sent a request to itself for a banner ad
* Classic Mac OS: please read this helpful information submitted by David “iNerd” B
* Mac OS 9: Marcia Skidmore sent in details that hopefully explain what you need to know
The format of the hosts file is very simple – IP address, whitespace, then a list of hostnames (except for older Macs; please see above). However, you don’t need to know anything about the format if you don’t want to as you can just view the list hosts file.
Of course, that’s not the only way to use the list, but it’s probably the most simple for most people.
Here is the hosts list which are serving you the ads just append it to your hosts file and enjoy ad free surfing makes things faster. If you want ad from certain site then just remove it from the list below.
You have to copy all these domain names from here and paste at the end of your hosts file. Here is a text file if you are lazy enough and dont want to copy all of them.
127.0.0.1 007arcadegames.com
127.0.0.1 101order.com
127.0.0.1 123banners.com
127.0.0.1 123found.com
127.0.0.1 180searchassistant.com
127.0.0.1 180solutions.com
127.0.0.1 247media.com
127.0.0.1 247realmedia.com
127.0.0.1 24pm-affiliation.com
127.0.0.1 2log.com
127.0.0.1 2o7.net
127.0.0.1 4affiliate.net
127.0.0.1 4d5.net
127.0.0.1 7adpower.com
127.0.0.1 911promotion.com
127.0.0.1 a-counter.kiev.ua
127.0.0.1 a.consumer.net
127.0.0.1 a.gismeteo.ru
127.0.0.1 a.mktw.net
127.0.0.1 a.r.tv.com
127.0.0.1 a.xanga.com
127.0.0.1 a32.g.a.yimg.com
127.0.0.1 aaddzz.com
127.0.0.1 abcnews.footprint.net
127.0.0.1 abetterinternet.com
127.0.0.1 abz.com
127.0.0.1 ac.rnm.ca
127.0.0.1 accelerator-media.com
127.0.0.1 accipiter.speedera.net
127.0.0.1 action.ientry.net
127.0.0.1 actionsplash.com
127.0.0.1 actualdeals.com
127.0.0.1 ad-annex.com
127.0.0.1 ad-flow.com
127.0.0.1 ad-images.suntimes.com
127.0.0.1 ad-logics.com
127.0.0.1 ad-rotator.com
127.0.0.1 ad-server.gulasidorna.se
127.0.0.1 ad-souk.com
127.0.0.1 ad-space.net
127.0.0.1 ad-tech.com
127.0.0.1 ad-universe.com
127.0.0.1 ad-up.com
127.0.0.1 ad.100.tbn.ru
127.0.0.1 ad.37.com
127.0.0.1 ad.4web.cz
127.0.0.1 ad.71i.de
127.0.0.1 ad.a8.net
127.0.0.1 ad.abcnews.com
127.0.0.1 ad.abctv.com
127.0.0.1 ad.about.com
127.0.0.1 ad.aboutit.de
127.0.0.1 ad.aboutwebservices.com
127.0.0.1 ad.aftonbladet.se
127.0.0.1 ad.allstar.cz
127.0.0.1 ad.altervista.org
127.0.0.1 ad.asap-asp.net
127.0.0.1 ad.bondage.com
127.0.0.1 ad.centrum.cz
127.0.0.1 ad.cgi.cz
127.0.0.1 ad.chip.de
127.0.0.1 ad.clix.pt
127.0.0.1 ad.digitallook.com
127.0.0.1 ad.directconnect.se
127.0.0.1 ad.disney.go.com
127.0.0.1 ad.domainfactory.de
127.0.0.1 ad.dvdforum.nu
127.0.0.1 ad.e-kolay.net
127.0.0.1 ad.e-not.net
127.0.0.1 ad.eurosport.com
127.0.0.1 ad.ezpeer.com
127.0.0.1 ad.fido.net
127.0.0.1 ad.fragzone.se
127.0.0.1 ad.free6.com
127.0.0.1 ad.grafika.cz
127.0.0.1 ad.harmony-central.com
127.0.0.1 ad.hbv.de
127.0.0.1 ad.howstuffworks.com
127.0.0.1 ad.hyena.cz
127.0.0.1 ad.iinfo.cz
127.0.0.1 ad.ilse.nl
127.0.0.1 ad.img.yahoo.co.kr
127.0.0.1 ad.infoseek.com
127.0.0.1 ad.investopedia.com
127.0.0.1 ad.ir.ru
127.0.0.1 ad.itmedia.co.jp
127.0.0.1 ad.jetsoftware.com
127.0.0.1 ad.keenspace.com
127.0.0.1 ad.krutilka.ru
127.0.0.1 ad.leadcrunch.com
127.0.0.1 ad.linx.cz
127.0.0.1 ad.liveinternet.ru
127.0.0.1 ad.lupa.cz
127.0.0.1 ad.mediastorm.hu
127.0.0.1 ad.mgd.de
127.0.0.1 ad.moscowtimes.ru
127.0.0.1 ad.musicmatch.com
127.0.0.1 ad.mwizard.net
127.0.0.1 ad.nachtagenten.de
127.0.0.1 ad.nozonedata.com
127.0.0.1 ad.nrk.no
127.0.0.1 ad.pbs.bb.ru
127.0.0.1 ad.playground.ru
127.0.0.1 ad.preferances.com
127.0.0.1 ad.rambler.ru
127.0.0.1 ad.reunion.com
127.0.0.1 ad.seznam.cz
127.0.0.1 ad.simgames.net
127.0.0.1 ad.spieletips.de
127.0.0.1 ad.suprnova.org
127.0.0.1 ad.surfsecret.com
127.0.0.1 ad.sweclockers.com
127.0.0.1 ad.t2t2.com
127.0.0.1 ad.tbn.ru
127.0.0.1 ad.tiscali.com
127.0.0.1 ad.tisnet.net.tw
127.0.0.1 ad.tomshardware.com
127.0.0.1 ad.top50.to
127.0.0.1 ad.tv2.no
127.0.0.1 ad.tweakpc.de
127.0.0.1 ad.uk.tangozebra.com
127.0.0.1 ad.uol.com.br
127.0.0.1 ad.usatoday.com
127.0.0.1 ad.way.cz
127.0.0.1 ad.wz.cz
127.0.0.1 ad.yadro.ru
127.0.0.1 ad.yieldmanager.com
127.0.0.1 ad.yourmedia.com
127.0.0.1 ad01.mediacorpsingapore.com
127.0.0.1 ad1.emediate.dk
127.0.0.1 ad1.gamezone.com
127.0.0.1 ad1.hardware.no
127.0.0.1 ad1.kde.cz
127.0.0.1 ad1.lbe.ru
127.0.0.1 ad1.outpost.com
127.0.0.1 ad1.zendmedia.com
127.0.0.1 ad2.atlas.cz
127.0.0.1 ad2.bb.ru
127.0.0.1 ad2.insitemedia.hu
127.0.0.1 ad2.lbe.ru
127.0.0.1 ad2.linx.cz
127.0.0.1 ad2.linxcz.cz
127.0.0.1 ad2.lupa.cz
127.0.0.1 ad2.mamma.com
127.0.0.1 ad2.seznam.cz
127.0.0.1 ad2.tisnet.net.tw
127.0.0.1 ad3.tisnet.net.tw
127.0.0.1 ad4.atlas.cz
127.0.0.1 ad4.tisnet.net.tw
127.0.0.1 ad41.atlas.cz
127.0.0.1 ad4ex.com
127.0.0.1 adbanner.ro
127.0.0.1 adboost.de.vu
127.0.0.1 adbot.com
127.0.0.1 adbot.theonion.com
127.0.0.1 adbrite.com
127.0.0.1 adbureau.net
127.0.0.1 adbutler.com
127.0.0.1 adbutler.de
127.0.0.1 adcell.de
127.0.0.1 adcenter.mdf.se
127.0.0.1 adcenter.net
127.0.0.1 adcentriconline.com
127.0.0.1 adcept.net
127.0.0.1 adclick.com
127.0.0.1 adclick.gamespy.com
127.0.0.1 adclick.mint.se
127.0.0.1 adclick.ro
127.0.0.1 adclient.rottentomatoes.com
127.0.0.1 adclient1.tucows.com
127.0.0.1 adcomplete.com
127.0.0.1 adcontent.gamespy.com
127.0.0.1 adcontroller.unicast.com
127.0.0.1 adcreative.tribuneinteractive.com
127.0.0.1 adcycle.com
127.0.0.1 adcycle.icpeurope.net
127.0.0.1 addcontrol.net
127.0.0.1 addesktop.com
127.0.0.1 addfreestats.com
127.0.0.1 addme.com
127.0.0.1 addynamix.com
127.0.0.1 adengage.com
127.0.0.1 adext.inkclub.com
127.0.0.1 adfarm.mediaplex.com
127.0.0.1 adfiles.api.no
127.0.0.1 adflight.com
127.0.0.1 adfly.com
127.0.0.1 adhostcenter.com
127.0.0.1 adi.mainichi.co.jp
127.0.0.1 adimage.asiaone.com.sg
127.0.0.1 adimages.been.com
127.0.0.1 adimages.carsoup.com
127.0.0.1 adimages.go.com
127.0.0.1 adimages.homestore.com
127.0.0.1 adimages.sanomawsoy.fi
127.0.0.1 adimg.cnet.com
127.0.0.1 adimg.com.com
127.0.0.1 adimg1.chosun.com
127.0.0.1 adimgs.sapo.pt
127.0.0.1 adincl.gopher.com
127.0.0.1 adition.de
127.0.0.1 adition.net
127.0.0.1 adjuggler.yourdictionary.com
127.0.0.1 adlegend.com
127.0.0.1 adlink.de
127.0.0.1 adlog.com.com
127.0.0.1 adlogix.net
127.0.0.1 adm.ad.asap-asp.net
127.0.0.1 adman.freeze.com
127.0.0.1 admanagement.ch
127.0.0.1 admanager.beweb.com
127.0.0.1 admanager.btopenworld.com
127.0.0.1 admanager.carsoup.com
127.0.0.1 admanager.persianblog.com
127.0.0.1 admaximize.com
127.0.0.1 admedia.ro
127.0.0.1 admeta.com
127.0.0.1 admex.com
127.0.0.1 adminder.com
127.0.0.1 adminshop.com
127.0.0.1 admonitor.com
127.0.0.1 admonitor.net
127.0.0.1 admotion.com.ar
127.0.0.1 adnet.biz
127.0.0.1 adnews.maddog2000.de
127.0.0.1 ado.internet.cz
127.0.0.1 adorigin.com
127.0.0.1 adpepper.dk
127.0.0.1 adpick.switchboard.com
127.0.0.1 adprofile.net
127.0.0.1 adprojekt.pl
127.0.0.1 adpush.dreamscape.com
127.0.0.1 adq.nextag.com
127.0.0.1 adremedy.com
127.0.0.1 adremote.pathfinder.com
127.0.0.1 adrenaline.cz
127.0.0.1 adrenalinesk.sk
127.0.0.1 adreporting.com
127.0.0.1 adres.internet.com
127.0.0.1 adrevolver.com
127.0.0.1 adrevolver.holzmannverlag.de
127.0.0.1 adriver.ru
127.0.0.1 adroar.com
127.0.0.1 adrotate.de
127.0.0.1 adrotator.net
127.0.0.1 ads-205.quarterserver.de
127.0.0.1 ads-de.spray.net
127.0.0.1 ads.100asians.com
127.0.0.1 ads.5ci.lt
127.0.0.1 ads.aceweb.net
127.0.0.1 ads.adshareware.net
127.0.0.1 ads.adultfriendfinder.com
127.0.0.1 ads.advance.net
127.0.0.1 ads.adverline.com
127.0.0.1 ads.affiliates.match.com
127.0.0.1 ads.allsites.com
127.0.0.1 ads.alwayson-network.com
127.0.0.1 ads.amazingmedia.com
127.0.0.1 ads.amdmb.com
127.0.0.1 ads.aol.com
127.0.0.1 ads.as4x.tmcs.net
127.0.0.1 ads.asia1.com.sg
127.0.0.1 ads.asiafriendfinder.com
127.0.0.1 ads.aspalliance.com
127.0.0.1 ads.battle.net
127.0.0.1 ads.belointeractive.com
127.0.0.1 ads.berlinonline.de
127.0.0.1 ads.betanews.com
127.0.0.1 ads.bfast.com
127.0.0.1 ads.bigcitytools.com
127.0.0.1 ads.bigfoot.com
127.0.0.1 ads.billiton.de
127.0.0.1 ads.bitsonthewire.com
127.0.0.1 ads.blick.ch
127.0.0.1 ads.bloomberg.com
127.0.0.1 ads.bluemountain.com
127.0.0.1 ads.box.sk
127.0.0.1 ads.businessweek.com
127.0.0.1 ads.canalblog.com
127.0.0.1 ads.canoe.ca
127.0.0.1 ads.cavello.com
127.0.0.1 ads.cbc.ca
127.0.0.1 ads.cdfreaks.com
127.0.0.1 ads.centraliprom.com
127.0.0.1 ads.cgnetworks.com
127.0.0.1 ads.channel4.com
127.0.0.1 ads.cimedia.com
127.0.0.1 ads.clearchannel.com
127.0.0.1 ads.collegclub.com
127.0.0.1 ads.com.com
127.0.0.1 ads.currantbun.com
127.0.0.1 ads.cyberfight.ru
127.0.0.1 ads.cybersales.cz
127.0.0.1 ads.danworld.net
127.0.0.1 ads.datingyes.com
127.0.0.1 ads.dbforums.com
127.0.0.1 ads.ddj.com
127.0.0.1 ads.deltha.hu
127.0.0.1 ads.dennisnet.co.uk
127.0.0.1 ads.desmoinesregister.com
127.0.0.1 ads.detelefoongids.nl
127.0.0.1 ads.developershed.com
127.0.0.1 ads.deviantart.com
127.0.0.1 ads.digitalmedianet.com
127.0.0.1 ads.digitalpoint.com
127.0.0.1 ads.directionsmag.com
127.0.0.1 ads.discovery.com
127.0.0.1 ads.dk
127.0.0.1 ads.dmk-internet.com
127.0.0.1 ads.e-planning.net
127.0.0.1 ads.edbindex.dk
127.0.0.1 ads.einmedia.com
127.0.0.1 ads.erotism.com
127.0.0.1 ads.esmas.com
127.0.0.1 ads.eu.msn.com
127.0.0.1 ads.eudora.com
127.0.0.1 ads.exhedra.com
127.0.0.1 ads.ezboard.com
127.0.0.1 ads.fairfax.com.au
127.0.0.1 ads.filmup.com
127.0.0.1 ads.firingsquad.com
127.0.0.1 ads.flooble.com
127.0.0.1 ads.floridatoday.com
127.0.0.1 ads.fool.com
127.0.0.1 ads.forbes.com
127.0.0.1 ads.forbes.net
127.0.0.1 ads.forium.de
127.0.0.1 ads.fortunecity.com
127.0.0.1 ads.foxkidseurope.net
127.0.0.1 ads.freecity.de
127.0.0.1 ads.freeze.com
127.0.0.1 ads.friendtest.com
127.0.0.1 ads.ft.com
127.0.0.1 ads.g4techtv.com
127.0.0.1 ads.game.net
127.0.0.1 ads.gamecity.net
127.0.0.1 ads.gamecopyworld.no
127.0.0.1 ads.gameforgeads.de
127.0.0.1 ads.gamershell.com
127.0.0.1 ads.gamespy.com
127.0.0.1 ads.gamespyid.com
127.0.0.1 ads.gamigo.de
127.0.0.1 ads.gawker.com
127.0.0.1 ads.gettools.com
127.0.0.1 ads.globeandmail.com
127.0.0.1 ads.gotfrag.com
127.0.0.1 ads.goyk.com
127.0.0.1 ads.grindinggears.com
127.0.0.1 ads.guardian.co.uk
127.0.0.1 ads.guardianunlimited.co.uk
127.0.0.1 ads.hbv.de
127.0.0.1 ads.heartlight.org
127.0.0.1 ads.herald-sun.com
127.0.0.1 ads.hollywood.com
127.0.0.1 ads.humorbua.no
127.0.0.1 ads.iafrica.com
127.0.0.1 ads.iboost.com
127.0.0.1 ads.icq.com
127.0.0.1 ads.ign.com
127.0.0.1 ads.imdb.com
127.0.0.1 ads.img.co.za
127.0.0.1 ads.indya.com
127.0.0.1 ads.indystar.com
127.0.0.1 ads.inetfast.com
127.0.0.1 ads.inetinteractive.com
127.0.0.1 ads.infi.net
127.0.0.1 ads.infospace.com
127.0.0.1 ads.internic.co.il
127.0.0.1 ads.inthemix.com.au
127.0.0.1 ads.ipowerweb.com
127.0.0.1 ads.isoftmarketing.com
127.0.0.1 ads.itv.com
127.0.0.1 ads.iwon.com
127.0.0.1 ads.jimworld.com
127.0.0.1 ads.jpost.com
127.0.0.1 ads.jubii.dk
127.0.0.1 ads.katz.ws
127.0.0.1 ads.kinobox.cz
127.0.0.1 ads.krawall.de
127.0.0.1 ads.leo.org
127.0.0.1 ads.linuxjournal.com
127.0.0.1 ads.linuxquestions.org
127.0.0.1 ads.linuxsecurity.com
127.0.0.1 ads.lnkworld.com
127.0.0.1 ads.localnow.com
127.0.0.1 ads.lycos-europe.com
127.0.0.1 ads.lycos.com
127.0.0.1 ads.madison.com
127.0.0.1 ads.mariuana.it
127.0.0.1 ads.mcafee.com
127.0.0.1 ads.mediaodyssey.com
127.0.0.1 ads.mediaturf.net
127.0.0.1 ads.metropol.dk
127.0.0.1 ads.mgnetwork.com
127.0.0.1 ads.monster.com
127.0.0.1 ads.msn.com
127.0.0.1 ads.multimania.lycos.fr
127.0.0.1 ads.musiccity.com
127.0.0.1 ads.myguysolutions.com
127.0.0.1 ads.mysimon.com
127.0.0.1 ads.nandomedia.com
127.0.0.1 ads.nationalreview.com
127.0.0.1 ads.neoseeker.com
127.0.0.1 ads.neowin.net
127.0.0.1 ads.netmechanic.com
127.0.0.1 ads.newcity.com
127.0.0.1 ads.newcitynet.com
127.0.0.1 ads.newdream.net
127.0.0.1 ads.newmedia.cz
127.0.0.1 ads.newsint.co.uk
127.0.0.1 ads.newsobserver.com
127.0.0.1 ads.newsquest.co.uk
127.0.0.1 ads.newtimes.com
127.0.0.1 ads.ngenuity.com
127.0.0.1 ads.ninemsn.com.au
127.0.0.1 ads.nola.com
127.0.0.1 ads.nordichardware.se
127.0.0.1 ads.ntadvice.com
127.0.0.1 ads.nwsource.com
127.0.0.1 ads.nyi.net
127.0.0.1 ads.nyjournalnews.com
127.0.0.1 ads.nypost.com
127.0.0.1 ads.nytimes.com
127.0.0.1 ads.nzcity.co.nz
127.0.0.1 ads.ole.com
127.0.0.1 ads.oneplace.com
127.0.0.1 ads.onlineguiden.com
127.0.0.1 ads.optusnet.com.au
127.0.0.1 ads.orsm.net
127.0.0.1 ads.osdn.com
127.0.0.1 ads.osnews.com
127.0.0.1 ads.ourbrisbane.com
127.0.0.1 ads.overclockers.at
127.0.0.1 ads.pcper.com
127.0.0.1 ads.peel.com
127.0.0.1 ads.phparena.net
127.0.0.1 ads.phpclasses.org
127.0.0.1 ads.pittsburghlive.com
127.0.0.1 ads.planet.nl
127.0.0.1 ads.pni.com
127.0.0.1 ads.powweb.com
127.0.0.1 ads.premiumnetwork.com
127.0.0.1 ads.primeinteractive.net
127.0.0.1 ads.prisacom.com
127.0.0.1 ads.pro-market.net
127.0.0.1 ads.realcities.com
127.0.0.1 ads.realmedia.de
127.0.0.1 ads.recoletos.es
127.0.0.1 ads.rediff.com
127.0.0.1 ads.rivals.net
127.0.0.1 ads.rottentomatoes.com
127.0.0.1 ads.rp-online.de
127.0.0.1 ads.rpgdot.com
127.0.0.1 ads.rpgui.com
127.0.0.1 ads.satyamonline.com
127.0.0.1 ads.savannahnow.com
127.0.0.1 ads.scifi.com
127.0.0.1 ads.sexplanets.com
127.0.0.1 ads.shareprovider.com
127.0.0.1 ads.sify.com
127.0.0.1 ads.simtel.net
127.0.0.1 ads.smartclick.com
127.0.0.1 ads.softwareoutfit.com
127.0.0.1 ads.space.com
127.0.0.1 ads.sptimes.com
127.0.0.1 ads.stationplay.com
127.0.0.1 ads.stileproject.com
127.0.0.1 ads.storagereview.net
127.0.0.1 ads.stratics.com
127.0.0.1 ads.switchboard.com
127.0.0.1 ads.techtv.com
127.0.0.1 ads.telegraaf.nl
127.0.0.1 ads.telegraph.co.uk
127.0.0.1 ads.theglobeandmail.com
127.0.0.1 ads.thestar.com
127.0.0.1 ads.thewebfreaks.com
127.0.0.1 ads.thottbot.com
127.0.0.1 ads.tiscali.fr
127.0.0.1 ads.tmcs.net
127.0.0.1 ads.top500.org
127.0.0.1 ads.townhall.com
127.0.0.1 ads.tripod.com
127.0.0.1 ads.tripod.lycos.co.uk
127.0.0.1 ads.tripod.lycos.de
127.0.0.1 ads.tripod.lycos.nl
127.0.0.1 ads.tucows.com
127.0.0.1 ads.ucomics.com
127.0.0.1 ads.uigc.net
127.0.0.1 ads.unixathome.org
127.0.0.1 ads.urli.net
127.0.0.1 ads.usatoday.com
127.0.0.1 ads.v3.com
127.0.0.1 ads.v3exchange.com
127.0.0.1 ads.vesperexchange.com
127.0.0.1 ads.videoaxs.com
127.0.0.1 ads.virtual-nights.com
127.0.0.1 ads.virtualcountries.com
127.0.0.1 ads.vnuemedia.com
127.0.0.1 ads.vnumedia.com
127.0.0.1 ads.wanadooregie.com
127.0.0.1 ads.weather.ca
127.0.0.1 ads.weather.com
127.0.0.1 ads.web.aol.com
127.0.0.1 ads.web.cs.com
127.0.0.1 ads.web.de
127.0.0.1 ads.web21.com
127.0.0.1 ads.webattack.com
127.0.0.1 ads.webheat.com
127.0.0.1 ads.webnet.advance.net
127.0.0.1 ads.whi.co.nz
127.0.0.1 ads.winsite.com
127.0.0.1 ads.wunderground.com
127.0.0.1 ads.x10.com
127.0.0.1 ads.x10.net
127.0.0.1 ads.xtra.co.nz
127.0.0.1 ads.yourfreedvds.com
127.0.0.1 ads.zdnet.com
127.0.0.1 ads001.webwombat.com.au
127.0.0.1 ads1.advance.net
127.0.0.1 ads1.akkuna.com
127.0.0.1 ads1.canoe.ca
127.0.0.1 ads1.erotism.com
127.0.0.1 ads1.mediacapital.pt
127.0.0.1 ads1.sptimes.com
127.0.0.1 ads1.theglobeandmail.com
127.0.0.1 ads10.speedbit.com
127.0.0.1 ads2.advance.net
127.0.0.1 ads2.akkuna.com
127.0.0.1 ads2.clearchannel.com
127.0.0.1 ads2.collegclub.com
127.0.0.1 ads2.collegeclub.com
127.0.0.1 ads2.exhedra.com
127.0.0.1 ads2.firingsquad.com
127.0.0.1 ads2.gamecity.net
127.0.0.1 ads2.jubii.dk
127.0.0.1 ads2.oneplace.com
127.0.0.1 ads2.osdn.com
127.0.0.1 ads2.top500.org
127.0.0.1 ads3.advance.net
127.0.0.1 ads3.gamecity.net
127.0.0.1 ads360.com
127.0.0.1 ads4.advance.net
127.0.0.1 ads4.clearchannel.com
127.0.0.1 ads4.gamecity.net
127.0.0.1 ads4.realcities.com
127.0.0.1 ads4homes.com
127.0.0.1 ads5.advance.net
127.0.0.1 ads5.canoe.ca
127.0.0.1 ads6.advance.net
127.0.0.1 ads6.gamecity.net
127.0.0.1 ads7.gamecity.net
127.0.0.1 ads8.com
127.0.0.1 adsag.com
127.0.0.1 Adsatt.ABCNews.starwave.com
127.0.0.1 adsatt.espn.go.com
127.0.0.1 adsatt.espn.starwave.com
127.0.0.1 Adsatt.go.starwave.com
127.0.0.1 adscholar.com
127.0.0.1 adscpm.com
127.0.0.1 adsdaq.com
127.0.0.1 adserv.aip.org
127.0.0.1 adserv.gamezone.de
127.0.0.1 adserv.geocomm.com
127.0.0.1 adserv.happypuppy.com
127.0.0.1 adserv.iafrica.com
127.0.0.1 adserv.lwmn.net
127.0.0.1 adserv.quality-channel.de
127.0.0.1 adserv1.winboard.org
127.0.0.1 adserve.viaarena.com
127.0.0.1 adserver.71i.de
127.0.0.1 adserver.adultfriendfinder.com
127.0.0.1 adserver.allerinternett.com
127.0.0.1 adserver.anm.co.uk
127.0.0.1 adserver.ath.cx
127.0.0.1 adserver.billiger-surfen.de
127.0.0.1 adserver.billiger-telefonieren.de
127.0.0.1 adserver.bluewin.ch
127.0.0.1 adserver.colleges.com
127.0.0.1 adserver.com
127.0.0.1 adserver.conjelco.com
127.0.0.1 adserver.developersnetwork.com
127.0.0.1 adserver.digitoday.com
127.0.0.1 adserver.dotcommedia.de
127.0.0.1 adserver.eudora.com
127.0.0.1 adserver.filefront.com
127.0.0.1 adserver.freecity.de
127.0.0.1 adserver.freenet.de
127.0.0.1 adserver.friendfinder.com
127.0.0.1 adserver.gamesquad.net
127.0.0.1 adserver.garden.com
127.0.0.1 adserver.geizkragen.de
127.0.0.1 adserver.gr
127.0.0.1 adserver.hardwareanalysis.com
127.0.0.1 adserver.hispavista.com
127.0.0.1 adserver.humanux.com
127.0.0.1 adserver.ign.com
127.0.0.1 adserver.isonews.com
127.0.0.1 adserver.itsfogo.com
127.0.0.1 adserver.janes.com
127.0.0.1 adserver.jolt.co.uk
127.0.0.1 adserver.journalinteractive.com
127.0.0.1 adserver.legacy-network.com
127.0.0.1 adserver.libero.it
127.0.0.1 adserver.m2kcore.com
127.0.0.1 adserver.monster.com
127.0.0.1 adserver.news.com.au
127.0.0.1 adserver.ngz-network.de
127.0.0.1 adserver.nydailynews.com
127.0.0.1 adserver.nzoom.com
127.0.0.1 adserver.pl
127.0.0.1 adserver.plhb.com
127.0.0.1 adserver.portalofevil.com
127.0.0.1 adserver.portugalmail.net
127.0.0.1 adserver.portugalmail.pt
127.0.0.1 adserver.ro
127.0.0.1 adserver.sanomawsoy.fi
127.0.0.1 adserver.securityfocus.com
127.0.0.1 adserver.sharewareonline.com
127.0.0.1 adserver.snowball.com
127.0.0.1 adserver.startnow.com
127.0.0.1 adserver.terra.es
127.0.0.1 adserver.theonering.net
127.0.0.1 adserver.track-star.com
127.0.0.1 adserver.trb.com
127.0.0.1 adserver.tribuneinteractive.com
127.0.0.1 adserver.ugo.com
127.0.0.1 adserver.usermagnet.com
127.0.0.1 adserver.visions.de
127.0.0.1 adserver.webhostlist.de
127.0.0.1 adserver.yahoo.com
127.0.0.1 adserver1-images.backbeatmedia.com
127.0.0.1 adserver1.backbeatmedia.com
127.0.0.1 adserver1.mediainsight.de
127.0.0.1 adserver1.ogilvy-interactive.de
127.0.0.1 adserver1.shareconnector.com
127.0.0.1 adserver2.mediainsight.de
127.0.0.1 adserver2.popdata.de
127.0.0.1 adserver3.eudora.com
127.0.0.1 adserver4.eudora.com
127.0.0.1 adserversolutions.com
127.0.0.1 adservervv.geizkragen.de
127.0.0.1 adserving.eleven-agency.com
127.0.0.1 adservingcentral.com
127.0.0.1 adsfac.net
127.0.0.1 adshadow.net
127.0.0.1 adsmart.co.uk
127.0.0.1 adsmart.com
127.0.0.1 adsmart.net
127.0.0.1 adsmusic.com
127.0.0.1 adsnew.userfriendly.org
127.0.0.1 adsoftware.com
127.0.0.1 adsoldier.com
127.0.0.1 adsp.ilse.nl
127.0.0.1 adspace.ro
127.0.0.1 adsremote.scripps.com
127.0.0.1 adsrv.iol.co.za
127.0.0.1 adsweb.tiscali.cz
127.0.0.1 adsynergy.com
127.0.0.1 adsystem.tt-forums.net
127.0.0.1 adtech.de
127.0.0.1 adtech.m7z.net
127.0.0.1 adtoma.com
127.0.0.1 adtrade.net
127.0.0.1 adtrading.de
127.0.0.1 adtrak.net
127.0.0.1 adtrix.com
127.0.0.1 adv-banner.libero.it
127.0.0.1 adv.for-ua.com
127.0.0.1 adv.freeonline.it
127.0.0.1 adv.hwupgrade.it
127.0.0.1 adv.isdn.cz
127.0.0.1 adv.surinter.net
127.0.0.1 adv.webmd.com
127.0.0.1 adv.wp.pl
127.0.0.1 adv.yo.cz
127.0.0.1 adv1.videoprofessor.com
127.0.0.1 advariant.com
127.0.0.1 adventory.com
127.0.0.1 adverity.com
127.0.0.1 adverserve.net
127.0.0.1 advert.bayarea.com
127.0.0.1 advert.hi-media.com
127.0.0.1 advert.hu
127.0.0.1 adverticum.com
127.0.0.1 adverticum.net
127.0.0.1 advertiseireland.com
127.0.0.1 advertising.com
127.0.0.1 advertising.se
127.0.0.1 advertisingbanners.com
127.0.0.1 advertmarket.com
127.0.0.1 advertmedia.de
127.0.0.1 advertpro.sitepoint.com
127.0.0.1 adverts.carltononline.com
127.0.0.1 advertserve.com
127.0.0.1 advertwizard.com
127.0.0.1 adview.ppro.de
127.0.0.1 adviva.net
127.0.0.1 advlab.it
127.0.0.1 advnt.com
127.0.0.1 advnt01.com
127.0.0.1 advnt02.com
127.0.0.1 advnt03.com
127.0.0.1 advnt04.com
127.0.0.1 advspot.com
127.0.0.1 adware.hu
127.0.0.1 adwealth.com
127.0.0.1 adweb.integctr.com
127.0.0.1 adworldnetwork.com
127.0.0.1 adworx.at
127.0.0.1 adx.allstar.cz
127.0.0.1 adx.arip.co.th
127.0.0.1 adx.atnext.com
127.0.0.1 adx.nu
127.0.0.1 ady.arip.co.th
127.0.0.1 adz.afterdawn.net
127.0.0.1 affiliate.1800flowers.com
127.0.0.1 affiliate.7host.com
127.0.0.1 affiliate.cfdebt.com
127.0.0.1 affiliate.doubleyourdating.com
127.0.0.1 affiliate.dtiserv.com
127.0.0.1 affiliate.gamestop.com
127.0.0.1 affiliate.grasscity.com
127.0.0.1 affiliate.travelnow.com
127.0.0.1 affiliate.viator.com
127.0.0.1 affiliatefuel.com
127.0.0.1 affiliates.allposters.com
127.0.0.1 affiliates.internationaljock.com
127.0.0.1 affiliatetracking.net
127.0.0.1 affiliplus.de
127.0.0.1 afiliados.submarino.com.br
127.0.0.1 ah-ha.com
127.0.0.1 aim4media.com
127.0.0.1 alladvantage.com
127.0.0.1 amedia.techies.com
127.0.0.1 app.lstdesign.com
127.0.0.1 arc1.msn.com
127.0.0.1 as.cmpnet.com
127.0.0.1 as.fotexnet.hu
127.0.0.1 as1.falkag.de
127.0.0.1 as2.falkag.de
127.0.0.1 as3.falkag.de
127.0.0.1 as4.falkag.de
127.0.0.1 as5000.com
127.0.0.1 asv.gameplanet.co.nz
127.0.0.1 atdmt.com
127.0.0.1 atwola.com
127.0.0.1 audit.median.hu
127.0.0.1 audit.webinform.hu
127.0.0.1 autohits.dk
127.0.0.1 avatarresources.com
127.0.0.1 avenuea.com
127.0.0.1 avres.net
127.0.0.1 awarez.net
127.0.0.1 awrz.net
127.0.0.1 azjmp.com
127.0.0.1 azoogleads.com
127.0.0.1 babs.tv2.dk
127.0.0.1 backbeatmedia.com
127.0.0.1 banerovec.cz
127.0.0.1 banex.cz
127.0.0.1 banik.redigy.cz
127.0.0.1 banman.cz
127.0.0.1 banner.ad.nu
127.0.0.1 banner.buempliz-online.ch
127.0.0.1 banner.casino.net
127.0.0.1 banner.casinodelrio.com
127.0.0.1 banner.coza.com
127.0.0.1 banner.cz
127.0.0.1 banner.easyspace.com
127.0.0.1 banner.elisa.net
127.0.0.1 banner.getgo.de
127.0.0.1 banner.img.co.za
127.0.0.1 banner.inyourpocket.com
127.0.0.1 banner.jobsahead.com
127.0.0.1 banner.kiev.ua
127.0.0.1 banner.linux.se
127.0.0.1 banner.media-system.de
127.0.0.1 banner.mindshare.de
127.0.0.1 banner.musikmedia.de
127.0.0.1 banner.nixnet.cz
127.0.0.1 banner.noblepoker.com
127.0.0.1 banner.northsky.com
127.0.0.1 banner.orb.net
127.0.0.1 banner.penguin.cz
127.0.0.1 banner.relcom.ru
127.0.0.1 banner.rojakpot.com
127.0.0.1 banner.t-online.de
127.0.0.1 banner.tanto.de
127.0.0.1 banner.tpage.com
127.0.0.1 banner.webmersion.com
127.0.0.1 banner4all.dk
127.0.0.1 bannerads.de
127.0.0.1 bannerads.zwire.com
127.0.0.1 bannerbank.ru
127.0.0.1 bannerbox.hu
127.0.0.1 bannerboxes.com
127.0.0.1 bannercommunity.de
127.0.0.1 bannerexchange.cjb.net
127.0.0.1 bannerhost.com
127.0.0.1 bannerhosts.com
127.0.0.1 bannerimage.com
127.0.0.1 bannerlandia.com.ar
127.0.0.1 bannermall.com
127.0.0.1 bannermarkt.nl
127.0.0.1 bannerpower.com
127.0.0.1 banners.adultfriendfinder.com
127.0.0.1 banners.amigos.com
127.0.0.1 banners.arachne.cz
127.0.0.1 banners.asiafriendfinder.com
127.0.0.1 banners.babylon-x.com
127.0.0.1 banners.babylonbucks.com
127.0.0.1 banners.bol.com.br
127.0.0.1 banners.clubseventeen.com
127.0.0.1 banners.czi.cz
127.0.0.1 banners.de.clara.net
127.0.0.1 banners.directnic.com
127.0.0.1 banners.dot.tk
127.0.0.1 banners.easydns.com
127.0.0.1 banners.ebay.com
127.0.0.1 banners.freett.com
127.0.0.1 banners.friendfinder.com
127.0.0.1 banners.friendsfinder.com
127.0.0.1 banners.hetnet.nl
127.0.0.1 banners.internetsexprovider.com
127.0.0.1 banners.iq.pl
127.0.0.1 banners.isoftmarketing.com
127.0.0.1 banners.kfmb.com
127.0.0.1 banners.lifeserv.com
127.0.0.1 banners.linkbuddies.com
127.0.0.1 banners.netcraft.com
127.0.0.1 banners.one2one.com
127.0.0.1 banners.resultonline.com
127.0.0.1 banners.sexsearch.com
127.0.0.1 banners.tucson.com
127.0.0.1 banners.uk.clara.net
127.0.0.1 banners.wunderground.com
127.0.0.1 bannerserver.com
127.0.0.1 bannerserver.gator.com
127.0.0.1 bannersgomlm.com
127.0.0.1 bannersng.yell.com
127.0.0.1 bannerspace.com
127.0.0.1 bannerswap.com
127.0.0.1 bannertesting.com
127.0.0.1 bannieres.acces-contenu.com
127.0.0.1 bans.bride.ru
127.0.0.1 bansrv1.n1media.com
127.0.0.1 barnesandnoble.bfast.com
127.0.0.1 bbmedia.cz
127.0.0.1 bbn.img.com.ua
127.0.0.1 bestsearch.net
127.0.0.1 bidclix.com
127.0.0.1 bidclix.net
127.0.0.1 bigads.guj.de
127.0.0.1 bigbangmedia.com
127.0.0.1 billboard.cz
127.0.0.1 bizad.nikkeibp.co.jp
127.0.0.1 bizban.net
127.0.0.1 blast4traffic.com
127.0.0.1 blazefind.com
127.0.0.1 blogads.com
127.0.0.1 bluehavenmedia.com
127.0.0.1 bluestreak.com
127.0.0.1 bm.annonce.cz
127.0.0.1 bn.bfast.com
127.0.0.1 bnr.volgocity.ru
127.0.0.1 boom.ro
127.0.0.1 bpath.com
127.0.0.1 bravenet.com
127.0.0.1 bridgetrack.com
127.0.0.1 british-banners.com
127.0.0.1 bs.yandex.ru
127.0.0.1 bs001.gmx.net
127.0.0.1 bs002.gmx.net
127.0.0.1 bs003.gmx.net
127.0.0.1 bs004.gmx.net
127.0.0.1 bs005.gmx.net
127.0.0.1 bs006.gmx.net
127.0.0.1 bs007.gmx.net
127.0.0.1 bs008.gmx.net
127.0.0.1 bs009.gmx.net
127.0.0.1 bs010.gmx.net
127.0.0.1 bs011.gmx.net
127.0.0.1 bs012.gmx.net
127.0.0.1 bs013.gmx.net
127.0.0.1 bs014.gmx.net
127.0.0.1 bs015.gmx.net
127.0.0.1 bs016.gmx.net
127.0.0.1 bs017.gmx.net
127.0.0.1 bs018.gmx.net
127.0.0.1 bs019.gmx.net
127.0.0.1 bs020.gmx.net
127.0.0.1 bs021.gmx.net
127.0.0.1 bs022.gmx.net
127.0.0.1 bs023.gmx.net
127.0.0.1 bs024.gmx.net
127.0.0.1 bs025.gmx.net
127.0.0.1 bs026.gmx.net
127.0.0.1 bs027.gmx.net
127.0.0.1 bs028.gmx.net
127.0.0.1 bs029.gmx.net
127.0.0.1 bs030.gmx.net
127.0.0.1 bs031.gmx.net
127.0.0.1 bs032.gmx.net
127.0.0.1 bs033.gmx.net
127.0.0.1 bs034.gmx.net
127.0.0.1 bs035.gmx.net
127.0.0.1 bs036.gmx.net
127.0.0.1 bs037.gmx.net
127.0.0.1 bs038.gmx.net
127.0.0.1 bs039.gmx.net
127.0.0.1 bs040.gmx.net
127.0.0.1 bs041.gmx.net
127.0.0.1 bs042.gmx.net
127.0.0.1 bs043.gmx.net
127.0.0.1 bs044.gmx.net
127.0.0.1 bs045.gmx.net
127.0.0.1 bs046.gmx.net
127.0.0.1 bs047.gmx.net
127.0.0.1 bs048.gmx.net
127.0.0.1 bs049.gmx.net
127.0.0.1 budsinc.com
127.0.0.1 burstnet.akadns.net
127.0.0.1 burstnet.com
127.0.0.1 businessfactory.prospero.com
127.0.0.1 c.bigmir.net
127.0.0.1 c1.nowlinux.com
127.0.0.1 candidclicks.com
127.0.0.1 casalemedia.com
127.0.0.1 casalmedia.com
127.0.0.1 cash4banner.com
127.0.0.1 cash4banner.de
127.0.0.1 cash4popup.de
127.0.0.1 cashfiesta.com
127.0.0.1 cashpartner.com
127.0.0.1 cashpartner.net
127.0.0.1 casinogames.com
127.0.0.1 casinorewards.com
127.0.0.1 casinotraffic.com
127.0.0.1 casinotreasure.com
127.0.0.1 cat.clx.ru
127.0.0.1 cben1.net
127.0.0.1 cbx.net
127.0.0.1 cdn2.adsdk.com
127.0.0.1 centrport.net
127.0.0.1 cgicounter.puretec.de
127.0.0.1 ch.questionmarket.com
127.0.0.1 chart.dk
127.0.0.1 checkm8.com
127.0.0.1 chestionar.ro
127.0.0.1 ciaoclick.com
127.0.0.1 cibleclick.com
127.0.0.1 cityads.telus.net
127.0.0.1 cj.com
127.0.0.1 cjbmanagement.com
127.0.0.1 claria.com
127.0.0.1 click-fr.com
127.0.0.1 click.absoluteagency.com
127.0.0.1 click.fool.co.uk
127.0.0.1 click.fool.com
127.0.0.1 click.go2net.com
127.0.0.1 click2freemoney.com
127.0.0.1 click2paid.com
127.0.0.1 click4click.com
127.0.0.1 clickability.com
127.0.0.1 clickagents.com
127.0.0.1 clickbank.com
127.0.0.1 clickbank.net
127.0.0.1 clickbroker.com
127.0.0.1 clickbrokers.com
127.0.0.1 clickcash.webpower.com
127.0.0.1 clickedyclick.com
127.0.0.1 clickfinders.com
127.0.0.1 clickforwebmasters.com
127.0.0.1 clickhere.foronlinegames.com
127.0.0.1 clickhereforcellphones.com
127.0.0.1 clickhouse.com
127.0.0.1 clickhype.com
127.0.0.1 clickmedia.ro
127.0.0.1 clicks.equantum.com
127.0.0.1 clicks.jackpot.com
127.0.0.1 clicks.mods.de
127.0.0.1 clicks.stripsaver.com
127.0.0.1 clickserve.cc-dt.com
127.0.0.1 clicksor.com
127.0.0.1 clickthrutraffic.com
127.0.0.1 clicktracks.com
127.0.0.1 clicktrade.com
127.0.0.1 clickxchange.com
127.0.0.1 clickz.com
127.0.0.1 clictrafic.com
127.0.0.1 clients.tbo.com
127.0.0.1 clixgalore.com
127.0.0.1 cnt.one.ru
127.0.0.1 cnt1.pocitadlo.cz
127.0.0.1 code-server.biz
127.0.0.1 colonize.com
127.0.0.1 comclick.com
127.0.0.1 commission-junction.com
127.0.0.1 commissionmonster.com
127.0.0.1 commonname.com
127.0.0.1 compactbanner.com
127.0.0.1 comprabanner.it
127.0.0.1 contextclick.com
127.0.0.1 cookies.cmpnet.com
127.0.0.1 cornflakes.pathfinder.com
127.0.0.1 count.rin.ru
127.0.0.1 counted.com
127.0.0.1 counter.bloke.com
127.0.0.1 counter.cnw.cz
127.0.0.1 counter.cz
127.0.0.1 counter.nowlinux.com
127.0.0.1 counter.rambler.ru
127.0.0.1 counter.search.bg
127.0.0.1 counter.times.lv
127.0.0.1 counter.webtrends.net
127.0.0.1 counter.yadro.ru
127.0.0.1 counters.honesty.com
127.0.0.1 counts.tucows.com
127.0.0.1 coupling-media.de
127.0.0.1 crazypopups.com
127.0.0.1 creative.whi.co.nz
127.0.0.1 creatives.as4x.tmcs.net
127.0.0.1 cserver.mii.instacontent.net
127.0.0.1 ctnetwork.hu
127.0.0.1 ctxtads.overture.com
127.0.0.1 custom-click.com
127.0.0.1 customad.cnn.com
127.0.0.1 cyberbounty.com
127.0.0.1 cybercount.com
127.0.0.1 cybereps.com
127.0.0.1 cybermonitor.com
127.0.0.1 cydoor.com
127.0.0.1 datingadvertising.com
127.0.0.1 dbbsrv.com
127.0.0.1 dcad.tnn.net
127.0.0.1 dclk.net
127.0.0.1 de.rottentomatoes.com
127.0.0.1 dealhelper.com
127.0.0.1 default-homepage-network.com
127.0.0.1 deloo.de
127.0.0.1 desktop.kazaa.com
127.0.0.1 dgm2.com
127.0.0.1 dgmaustralia.com
127.0.0.1 dialerporn.com
127.0.0.1 didtheyreadit.com
127.0.0.1 digits.com
127.0.0.1 direct-revenue.com
127.0.0.1 direct.lbe.ru
127.0.0.1 directleads.com
127.0.0.1 directtrack.com
127.0.0.1 directwebsearch.net
127.0.0.1 discountclick.com
127.0.0.1 divicash.com
127.0.0.1 dnads.directnic.com
127.0.0.1 domainsponsor.com
127.0.0.1 domainsteam.de
127.0.0.1 doubleclic.com
127.0.0.1 doubleclick.com
127.0.0.1 doubleclick.de
127.0.0.1 doubleclick.net
127.0.0.1 drinkmy.com
127.0.0.1 dw.com.com
127.0.0.1 e-bannerx.com
127.0.0.1 e2give.com
127.0.0.1 eadexchange.com
127.0.0.1 eads.com
127.0.0.1 ecoupons.com
127.0.0.1 elitetoplist.com
127.0.0.1 emarketer.com
127.0.0.1 emarketmakers.com
127.0.0.1 engage.everyone.net
127.0.0.1 engage.omaha.com
127.0.0.1 engine.awaps.net
127.0.0.1 engine.espace.netavenir.com
127.0.0.1 enginenetwork.com
127.0.0.1 entercasino.com
127.0.0.1 erotic-ad.com
127.0.0.1 escati.linkopp.net
127.0.0.1 eshopads2.com
127.0.0.1 espotting.com
127.0.0.1 estats.com
127.0.0.1 etracker.de
127.0.0.1 eu-adcenter.net
127.0.0.1 euniverseads.com
127.0.0.1 euro4banner.com
127.0.0.1 europeanbanners.com
127.0.0.1 euros4click.de
127.0.0.1 eusta.de
127.0.0.1 exchange-it.com
127.0.0.1 exchange.bg
127.0.0.1 exchangead.com
127.0.0.1 exchangeclicksonline.com
127.0.0.1 exit76.com
127.0.0.1 exitexchange.com
127.0.0.1 exitfuel.com
127.0.0.1 ext4.price.ru
127.0.0.1 extreme-dm.com
127.0.0.1 eyeblaster-bs.com
127.0.0.1 eyeblaster.com
127.0.0.1 eyewonder.com
127.0.0.1 ezula.com
127.0.0.1 f1organizer.com
127.0.0.1 falkag.de
127.0.0.1 falkag.net
127.0.0.1 fast-adv.it
127.0.0.1 fastclick.com
127.0.0.1 fastclick.com.edgesuite.net
127.0.0.1 fastclick.net
127.0.0.1 fastcounter.bcentral.com
127.0.0.1 feedbackresearch.com
127.0.0.1 ffxcam.fairfax.com.au
127.0.0.1 findcommerce.com
127.0.0.1 findyourcasino.com
127.0.0.1 fineclicks.com
127.0.0.1 first.nova.cz
127.0.0.1 flexbanner.com
127.0.0.1 flowgo.com
127.0.0.1 fmads.osdn.com
127.0.0.1 focalex.com
127.0.0.1 fragmentserv.iac-online.de
127.0.0.1 free-banners.com
127.0.0.1 freebanner.com
127.0.0.1 freelogs.com
127.0.0.1 freestat.pl
127.0.0.1 freestats.com
127.0.0.1 freewebcounter.com
127.0.0.1 *BLEEP*-access.com
127.0.0.1 g-wizzads.net
127.0.0.1 galaxien.com
127.0.0.1 gamblingbanner.com
127.0.0.1 gamehouse.com
127.0.0.1 gator.com
127.0.0.1 gcads.osdn.com
127.0.0.1 gcirm.californianonline.com
127.0.0.1 gemius.pl
127.0.0.1 giftsky.org
127.0.0.1 globaltrack.com
127.0.0.1 go-clicks.de
127.0.0.1 goingplatinum.com
127.0.0.1 gold.weborama.fr
127.0.0.1 goldstats.com
127.0.0.1 googlesyndication.com
127.0.0.1 googleadservices.com
127.0.0.1 gorillanation.com
127.0.0.1 gostats.com
127.0.0.1 gp.dejanews.com
127.0.0.1 grafstat.ro
127.0.0.1 herbalaffiliateprogram.com
127.0.0.1 hexusads.fluent.ltd.uk
127.0.0.1 hightrafficads.com
127.0.0.1 hit.bg
127.0.0.1 hit.gemius.pl
127.0.0.1 hit.webcentre.lycos.co.uk
127.0.0.1 hitbox.com
127.0.0.1 hitcents.com
127.0.0.1 hitexchange.net
127.0.0.1 hitfarm.com
127.0.0.1 hitlist.ru
127.0.0.1 hitlogger.com
127.0.0.1 hitlounge.com
127.0.0.1 hitometer.com
127.0.0.1 hits4me.com
127.0.0.1 hitslink.com
127.0.0.1 hotlog.ru
127.0.0.1 hotrank.com.tw
127.0.0.1 hotstatistics.com
127.0.0.1 httpads.com
127.0.0.1 httpool.com
127.0.0.1 humanclick.com
127.0.0.1 hurricanedigitalmedia.com
127.0.0.1 hyperbanner.net
127.0.0.1 hypercount.com
127.0.0.1 i-clicks.net
127.0.0.1 i1img.com
127.0.0.1 iad.liveperson.net
127.0.0.1 iadnet.com
127.0.0.1 idot.cz
127.0.0.1 igads.no.publicus.com
127.0.0.1 ilbanner.com
127.0.0.1 ilead.itrack.it
127.0.0.1 iliillliO00OO0.321.cn
127.0.0.1 image.ugo.com
127.0.0.1 imageads.canoe.ca
127.0.0.1 images.v3.com
127.0.0.1 imaginemedia.com
127.0.0.1 img.bannersxchange.com
127.0.0.1 imonitor.nethost.cz
127.0.0.1 imprese.cz
127.0.0.1 impressionz.co.uk
127.0.0.1 imrworldwide.com
127.0.0.1 inboxdollars.com
127.0.0.1 inc.com
127.0.0.1 indieclick.com
127.0.0.1 industrybrains.com
127.0.0.1 inet-traffic.com
127.0.0.1 infinite-ads.com
127.0.0.1 information.com
127.0.0.1 infolinks.com
127.0.0.1 insightexpress.com
127.0.0.1 instacontent.net
127.0.0.1 instantmadness.com
127.0.0.1 intelliads.com
127.0.0.1 intellitxt.com
127.0.0.1 internet-optimizer.com
127.0.0.1 internetfuel.com
127.0.0.1 interreklame.de
127.0.0.1 ip.ro
127.0.0.1 ireklama.cz
127.0.0.1 is.casalemedia.com
127.0.0.1 itadnetwork.co.uk
127.0.0.1 itbannerexchange.com
127.0.0.1 itfarm.com
127.0.0.1 itop.cz
127.0.0.1 iwin.com
127.0.0.1 j.2004cms.com
127.0.0.1 jbeet.cjt1.net
127.0.0.1 jcontent.bns1.net
127.0.0.1 jcount.com
127.0.0.1 jedonkey.cjt1.net
127.0.0.1 jinisearch.co.uk
127.0.0.1 jkazaa.cjt1.net
127.0.0.1 jnova.cjt1.net
127.0.0.1 joetec.net
127.0.0.1 jokedollars.com
127.0.0.1 justwebads.com
127.0.0.1 kanoodle.com
127.0.0.1 kliks.nl
127.0.0.1 klipads.dvlabs.com
127.0.0.1 kliptracker.com
127.0.0.1 klix.cz
127.0.0.1 labeldaily.com
127.0.0.1 laih.com
127.0.0.1 lbn.ru
127.0.0.1 leadingedgecash.com
127.0.0.1 lightningcast.net
127.0.0.1 lightspeedcash.com
127.0.0.1 link4ads.com
127.0.0.1 linkbuddies.com
127.0.0.1 linkexchange.com
127.0.0.1 linkexchange.ru
127.0.0.1 linkprice.com
127.0.0.1 linkreferral.com
127.0.0.1 linksponsor.com
127.0.0.1 linkswaper.com
127.0.0.1 linksynergy.com
127.0.0.1 liquidad.narrowcastmedia.com
127.0.0.1 lnads.osdn.com
127.0.0.1 log.btopenworld.com
127.0.0.1 log.go.com
127.0.0.1 logging.to
127.0.0.1 logs.erasmas.com
127.0.0.1 look2me.com
127.0.0.1 lop.com
127.0.0.1 lstat.susanin.com
127.0.0.1 m.doubleclick.net
127.0.0.1 mads.gamespot.com
127.0.0.1 mainos2.mtv3.fi
127.0.0.1 marketbanker.com
127.0.0.1 marketing.centrebet.com
127.0.0.1 marketing.nyi.com
127.0.0.1 marketing.nyi.net
127.0.0.1 marketscore.com
127.0.0.1 mastermind.com
127.0.0.1 masterstats.com
127.0.0.1 matchcraft.com
127.0.0.1 maximumcash.com
127.0.0.1 maxserving.com
127.0.0.1 mbuyu.nl
127.0.0.1 media-adrunner.mycomputer.com
127.0.0.1 media-motor.net
127.0.0.1 media.bigstep.com
127.0.0.1 media.ftv-publicite.fr
127.0.0.1 mediacharger.com
127.0.0.1 mediadvertising.ro
127.0.0.1 mediageneral.com
127.0.0.1 mediamgr.ugo.com
127.0.0.1 mediaplazza.com
127.0.0.1 mediaplex.com
127.0.0.1 mediascale.de
127.0.0.1 mediavantage.de
127.0.0.1 megacash.de
127.0.0.1 megago.com
127.0.0.1 megawerbung.de
127.0.0.1 memorix.sdv.fr
127.0.0.1 metaad.econet.hu
127.0.0.1 metrics.webcriteria.net
127.0.0.1 microstatic.pl
127.0.0.1 microticker.com
127.0.0.1 mindseti.com
127.0.0.1 mirror.qkimg.net
127.0.0.1 mjxads.internet.com
127.0.0.1 mkt.cz
127.0.0.1 mojobucks.com
127.0.0.1 monsterpops.com
127.0.0.1 mostcash.com
127.0.0.1 ms-links.com
127.0.0.1 msads.net
127.0.0.1 mtree.com
127.0.0.1 multi1.rmuk.co.uk
127.0.0.1 musiccounter.ru
127.0.0.1 myaffiliateprogram.com
127.0.0.1 mystat.pl
127.0.0.1 mytrix.com
127.0.0.1 n69.com
127.0.0.1 naj.sk
127.0.0.1 navrcholu.cz
127.0.0.1 nedstat.com
127.0.0.1 nedstat.nl
127.0.0.1 nedstatbasic.net
127.0.0.1 netads.hotwired.com
127.0.0.1 netads.sohu.com
127.0.0.1 netdirect.nl
127.0.0.1 netpool.netbookia.net
127.0.0.1 netvertising.be
127.0.0.1 network.realmedia.com
127.0.0.1 new-ads.eurogamer.net
127.0.0.1 newads.cmpnet.com
127.0.0.1 newnet.qsrch.com
127.0.0.1 newtopsites.com
127.0.0.1 ng3.ads.warnerbros.com
127.0.0.1 ngadcenter.net
127.0.0.1 nitroclicks.com
127.0.0.1 nsads.hotwired.com
127.0.0.1 ntbanner.digitalriver.com
127.0.0.1 oas-central.realmedia.com
127.0.0.1 oas.benchmark.fr
127.0.0.1 oas.foxnews.com
127.0.0.1 oas.roanoke.com
127.0.0.1 oas.salon.com
127.0.0.1 oas.signonsandiego.com
127.0.0.1 oas.toronto.com
127.0.0.1 oas.uniontrib.com
127.0.0.1 oas.villagevoice.com
127.0.0.1 oascentral.chicagobusiness.com
127.0.0.1 oascentral.redherring.com
127.0.0.1 oascentral.theonion.com
127.0.0.1 oascentral.thesmokinggun.com
127.0.0.1 oasis.promon.cz
127.0.0.1 observer.cz
127.0.0.1 offeroptimizer.com
127.0.0.1 oneandonlynetwork.com
127.0.0.1 onestat.com
127.0.0.1 onresponse.com
127.0.0.1 openad.infobel.com
127.0.0.1 openad.travelnow.com
127.0.0.1 overpeer.com
127.0.0.1 overpro.com
127.0.0.1 overture.com
127.0.0.1 oxcash.com
127.0.0.1 p5.omaha.com
127.0.0.1 partner-ads.com
127.0.0.1 partner-source.com
127.0.0.1 partner.gonamic.de
127.0.0.1 partner.topcities.com
127.0.0.1 partner2profit.com
127.0.0.1 partnerkonto.de
127.0.0.1 partners.priceline.com
127.0.0.1 partners.starnetsystems.net
127.0.0.1 paycounter.com
127.0.0.1 paypopup.com
127.0.0.1 payserve.com
127.0.0.1 pbnet.ru
127.0.0.1 pcwizz.com
127.0.0.1 pennyweb.com
127.0.0.1 phoenix-adrunner.mycomputer.com
127.0.0.1 phpads.i-merge.net
127.0.0.1 pillscash.com
127.0.0.1 pimproll.com
127.0.0.1 planetactive.com
127.0.0.1 play4traffic.com
127.0.0.1 pointroll.com
127.0.0.1 pops.freeze.com
127.0.0.1 popup.msn.com
127.0.0.1 popupad.net
127.0.0.1 popupmoney.com
127.0.0.1 popupnation.com
127.0.0.1 popups.infostart.com
127.0.0.1 popupsponsor.com
127.0.0.1 popuptraffic.com
127.0.0.1 porntrack.com
127.0.0.1 postmasterbannernet.com
127.0.0.1 precisioncounter.com
127.0.0.1 premium-offers.com
127.0.0.1 premiumcash.de
127.0.0.1 primaryads.com
127.0.0.1 primetime.net
127.0.0.1 pro-advertising.com
127.0.0.1 profero.com
127.0.0.1 professorbanner.com
127.0.0.1 promote.pair.com
127.0.0.1 promozia.de
127.0.0.1 provexia.com
127.0.0.1 psstt.com
127.0.0.1 pub-g.ifrance.com
127.0.0.1 pub.club-internet.fr
127.0.0.1 pub.hardware.fr
127.0.0.1 pub.realmedia.fr
127.0.0.1 publi.grupocorreo.es
127.0.0.1 publi1.grupocorreo.es
127.0.0.1 publi2.grupocorreo.es
127.0.0.1 publiads.com
127.0.0.1 publicidad.elmundo.es
127.0.0.1 publicidad.ya.com
127.0.0.1 pubs.branchez-vous.com
127.0.0.1 pubs.lemonde.fr
127.0.0.1 q.azcentral.com
127.0.0.1 qckjmp.com
127.0.0.1 qksrv.net
127.0.0.1 quarterserver.de
127.0.0.1 questaffiliates.net
127.0.0.1 quinst.com
127.0.0.1 r.hotwired.com
127.0.0.1 r.kde.cz
127.0.0.1 rad.msn.com
127.0.0.1 radiate.com
127.0.0.1 rampidads.com
127.0.0.1 ranking-charts.de
127.0.0.1 ranking-hits.de
127.0.0.1 rankyou.com
127.0.0.1 rate.ru
127.0.0.1 rb1.design.ru
127.0.0.1 realads.realmedia.com
127.0.0.1 realclix.com
127.0.0.1 realmedia-a800.d4p.net
127.0.0.1 realtechnetwork.com
127.0.0.1 realtechnetwork.net
127.0.0.1 realtracker.com
127.0.0.1 redsherriff.com
127.0.0.1 referralware.com
127.0.0.1 regnow.com
127.0.0.1 reklam.rfsl.se
127.0.0.1 reklama.internet.cz
127.0.0.1 reklama.reflektor.cz
127.0.0.1 relmaxtop.com
127.0.0.1 remotead.cnet.com
127.0.0.1 reply.mediatris.net
127.0.0.1 retaildirect.realmedia.com
127.0.0.1 revenue.net
127.0.0.1 rewardster.com
127.0.0.1 richmails.com
127.0.0.1 richwebmaster.com
127.0.0.1 rightmedia.net
127.0.0.1 rightstats.com
127.0.0.1 rl.auto.ru
127.0.0.1 rle.ru
127.0.0.1 rmads.msn.com
127.0.0.1 rmedia.boston.com
127.0.0.1 rnd.yxo.ru
127.0.0.1 roar.com
127.0.0.1 roings.com
127.0.0.1 roosevelt.gjbig.com
127.0.0.1 rose.ixbt.com
127.0.0.1 rotabanner.dni.ru
127.0.0.1 rotabanner.izvestia.ru
127.0.0.1 rotabanner.rian.ru
127.0.0.1 rpts.net
127.0.0.1 ru-traffic.com
127.0.0.1 ru4.com
127.0.0.1 safe-audit.com
127.0.0.1 safelists.com
127.0.0.1 sageanalyst.net
127.0.0.1 searchlocate.com
127.0.0.1 searchramp.com
127.0.0.1 secure.webconnect.net
127.0.0.1 seeq.com
127.0.0.1 seo4india.com
127.0.0.1 separtnership.com
127.0.0.1 serv0.com
127.0.0.1 servads.aip.org
127.0.0.1 servedby.netshelter.net
127.0.0.1 servethis.com
127.0.0.1 serving-sys.com
127.0.0.1 sexcounter.com
127.0.0.1 sexlist.com
127.0.0.1 sextracker.com
127.0.0.1 sfads.osdn.com
127.0.0.1 shareasale.com
127.0.0.1 sher.index.hu
127.0.0.1 shinystat.it
127.0.0.1 siccash.com
127.0.0.1 sidebar.angelfire.com
127.0.0.1 sitemeter.com
127.0.0.1 sma.punto.net
127.0.0.1 smartadserver.com
127.0.0.1 smartclicks.net
127.0.0.1 smartdirect.com
127.0.0.1 smfgroup.cjb.net
127.0.0.1 smile.modchipstore.com
127.0.0.1 sn.baventures.com
127.0.0.1 softclick.com.br
127.0.0.1 software.global-netcom.de
127.0.0.1 softwaresponsor.com
127.0.0.1 specificclick.com
127.0.0.1 specificpop.com
127.0.0.1 spezialreporte.de
127.0.0.1 spinbox.maccentral.com
127.0.0.1 spinbox.net
127.0.0.1 spinbox.techtracker.com
127.0.0.1 spinbox.versiontracker.com
127.0.0.1 sponsor4you.net
127.0.0.1 sponsoradulto.com
127.0.0.1 sponsorpro.de
127.0.0.1 sponsors.thoughtsmedia.com
127.0.0.1 sprinks-clicks.about.com
127.0.0.1 spylog.com
127.0.0.1 spywarelabs.com
127.0.0.1 spywarenuker.com
127.0.0.1 ssads.osdn.com
127.0.0.1 starffa.com
127.0.0.1 start.freeze.com
127.0.0.1 stat.dealtime.com
127.0.0.1 stat.doxod.net
127.0.0.1 stat.pl
127.0.0.1 stat.webmedia.pl
127.0.0.1 stat.zenon.net
127.0.0.1 statcounter.com
127.0.0.1 static.itrack.it
127.0.0.1 static.smni.com
127.0.0.1 staticads.btopenworld.com
127.0.0.1 stats.blogger.com
127.0.0.1 stats.cts-bv.nl
127.0.0.1 stats.darkbluesea.com
127.0.0.1 stats.klsoft.com
127.0.0.1 stats4all.com
127.0.0.1 stop-popup-ads-now.com
127.0.0.1 sugoicounter.com
127.0.0.1 superclix.de
127.0.0.1 superstats.com
127.0.0.1 supertop.ru
127.0.0.1 supertop100.com
127.0.0.1 synergiinteractive.com
127.0.0.1 targad.de
127.0.0.1 targetnet.com
127.0.0.1 targetpoint.com
127.0.0.1 targetsaver.com
127.0.0.1 targetshop.com
127.0.0.1 teknosurf2.com
127.0.0.1 teknosurf3.com
127.0.0.1 test.com
127.0.0.1 textads.biz
127.0.0.1 textads.opera.com
127.0.0.1 textlinks.com
127.0.0.1 tfag.de
127.0.0.1 the-counter.net
127.0.0.1 theanswerto.com
127.0.0.1 thebannerguru.com
127.0.0.1 thecounter.com
127.0.0.1 thevictorynetwork.com
127.0.0.1 thinkingmedia.net
127.0.0.1 thisbanner.com
127.0.0.1 thruport.com
127.0.0.1 tier1network.com
127.0.0.1 tinybar.com
127.0.0.1 tmsads.tribune.com
127.0.0.1 toads.osdn.com
127.0.0.1 toolbar.netscape.com
127.0.0.1 top.list.ru
127.0.0.1 top.one.ru
127.0.0.1 top.proext.com
127.0.0.1 top100-images.rambler.ru
127.0.0.1 top100.mafia.ru
127.0.0.1 top20.com
127.0.0.1 topbarh.box.sk
127.0.0.1 toplist.cz
127.0.0.1 toplista.mw.hu
127.0.0.1 topping.com.ua
127.0.0.1 topprofits.info
127.0.0.1 toprebates.com
127.0.0.1 topsearcher.com
127.0.0.1 topshop-counter.rambler.ru
127.0.0.1 topstats.com
127.0.0.1 topstats.net
127.0.0.1 tps108.org
127.0.0.1 track.freexxxhost.net
127.0.0.1 tracking.frantic.com
127.0.0.1 tracking101.com
127.0.0.1 trackmysales.com
127.0.0.1 tradedoubler.com
127.0.0.1 traffic-exchange.com
127.0.0.1 trafficdiscount.com
127.0.0.1 trafficmp.com
127.0.0.1 trafficswarm.com
127.0.0.1 trafficsyndicate.com
127.0.0.1 traffictrader.net
127.0.0.1 trafficvenue.net
127.0.0.1 trafic.ro
127.0.0.1 traficdublu.ro
127.0.0.1 trafix.sk
127.0.0.1 trakkerd.net
127.0.0.1 trekblue.com
127.0.0.1 trekdata.com
127.0.0.1 tribalfusion.com
127.0.0.1 trix.net
127.0.0.1 truehits.net
127.0.0.1 truehits1.gits.net.th
127.0.0.1 truehits2.gits.net.th
127.0.0.1 tsms-ad.tsms.com
127.0.0.1 ukaffiliates2.com
127.0.0.1 ukbanners.com
127.0.0.1 ultimatecounter.com
127.0.0.1 updated.com
127.0.0.1 us.a1.yimg.com
127.0.0.1 usapromotravel.com
127.0.0.1 usmsad.tom.com
127.0.0.1 utarget.co.uk
127.0.0.1 utils.mediageneral.net
127.0.0.1 valuead.com
127.0.0.1 valueclick.com
127.0.0.1 valueclick.net
127.0.0.1 valuecommerce.com
127.0.0.1 valuesponsor.com
127.0.0.1 vendaregroup.com
127.0.0.1 vericlick.com
127.0.0.1 vg.ad.asap-asp.net
127.0.0.1 vibrantmedia.com
127.0.0.1 view4cash.de
127.0.0.1 viewpoint.com
127.0.0.1 vortextraffic.com
127.0.0.1 vx2.cc
127.0.0.1 w3exit.com
127.0.0.1 wannaclick.com
127.0.0.1 web-stat.com
127.0.0.1 web2.deja.com
127.0.0.1 webads.bizservers.com
127.0.0.1 webads.co.nz
127.0.0.1 webads.nl
127.0.0.1 webangel.ru
127.0.0.1 webcash.nl
127.0.0.1 webcounter.cz
127.0.0.1 webcounter.goweb.de
127.0.0.1 webmasterplan.com
127.0.0.1 webpdp.gator.com
127.0.0.1 webpower.com
127.0.0.1 websitefreepromotions.com
127.0.0.1 websponsors.com
127.0.0.1 webstars2000.com
127.0.0.1 webstat.com
127.0.0.1 webstat.net
127.0.0.1 webtraxx.de
127.0.0.1 webtrendslive.com
127.0.0.1 wegcash.com
127.0.0.1 wenksdisdkjeilsow.com
127.0.0.1 whenu.com
127.0.0.1 whispa.com
127.0.0.1 window.nixnet.cz
127.0.0.1 windupdates.com
127.0.0.1 wipub.com
127.0.0.1 worldbe.com
127.0.0.1 wtlive.com
127.0.0.1 wustat.windows.com
127.0.0.1 www-banner.chat.ru
127.0.0.1 www.adsxchange.lv
127.0.0.1 www.banner-link.com.br
127.0.0.1 www.dnps.com
127.0.0.1 www.kaplanindex.com
127.0.0.1 www.money4exit.de
127.0.0.1 www.photo-ads.co.uk
127.0.0.1 www.sponsor2002.de
127.0.0.1 x.mycity.com
127.0.0.1 xchange.ro
127.0.0.1 xiti.com
127.0.0.1 xq1.net
127.0.0.1 xtrocash.org
127.0.0.1 xxxcounter.com
127.0.0.1 xxxtoolbar.com
127.0.0.1 xzoomy.com
127.0.0.1 y.ibsys.com
127.0.0.1 yesadvertising.com
127.0.0.1 youclick2earn.com
127.0.0.1 z.times.lv
127.0.0.1 zanox-affiliate.de
127.0.0.1 zanox.com
127.0.0.1 zeads.com
127.0.0.1 zedo.com
127.0.0.1 zencudo.co.uk
127.0.0.1 zi.r.tv.com
127.0.0.1 zmedia.com
 You also get plenty of widgets for your homescreen to choose from, including a very nice lockscreen widget. You can customise the amount of information to be displayed on the lockscreen widget too, from album art to equaliser controls. Poweramp also gives you the option to change the theme. You get a bunch of them by default and you can even install third party themes from the Play Store. One feature that we feel should be added is a social component. Apps like MixZing allow you to play your music from your library as well as search for trending tracks around the globe. You can even see what your friends are listening to at the moment and rate songs so your friends can find them.
You also get plenty of widgets for your homescreen to choose from, including a very nice lockscreen widget. You can customise the amount of information to be displayed on the lockscreen widget too, from album art to equaliser controls. Poweramp also gives you the option to change the theme. You get a bunch of them by default and you can even install third party themes from the Play Store. One feature that we feel should be added is a social component. Apps like MixZing allow you to play your music from your library as well as search for trending tracks around the globe. You can even see what your friends are listening to at the moment and rate songs so your friends can find them.