Introduction
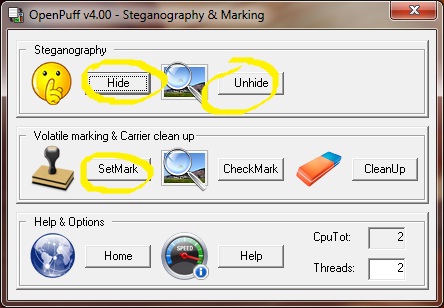
Due to the way different file types are read it is possible to have a single file that acts differently depending on how it is read. For example sounds & images are read from the header down whereas ZIP files are read from the footer up.
All sound files should work, but some are more unpredictable that others. Mp3s seem to be the most reliable so this tutorial will be using them in the examples (plus who doesn’t love mp3 songs). All the steps are same if you want to use an image(.jpg) instead of sound.
How to create one
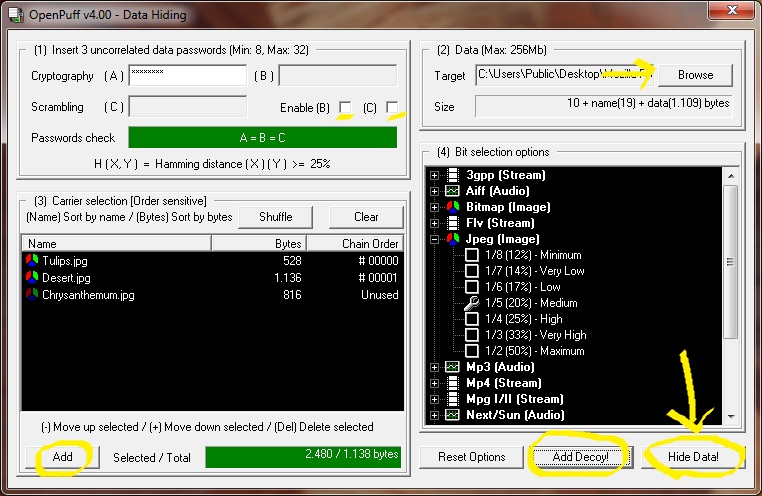
Firstly get hold of a sound file you want to hide the data in (example sound.mp3), then gather all your files you want to hide and put them in a ZIP (example secret.zip).
Our chosen Sound and zip file:
Windows 7: Shift+right click in the folder containing the files will open command prompt in that directory Windows: Open command prompt (start->run cmd), then use cd to get to the folder where the files are stored. Linux: You know what to do, open terminal and move to directory containing files.
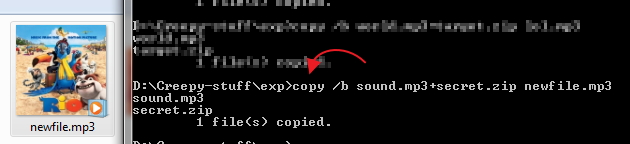
We now need to merge these files together, but we want to use a binary merge to keep the two files intact. With Windows copy command this uses the /B switch. (Binary Data)
Windows
Code:
Linux
Code:
You should now have gained a new file called newfile.mp3. This should look identical to the sound you started with when opened with a media player, but with a secret payload hidden within. Here is the example sound containing a ZIP:
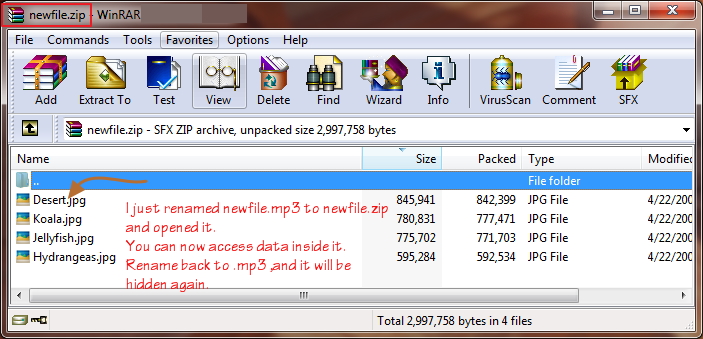
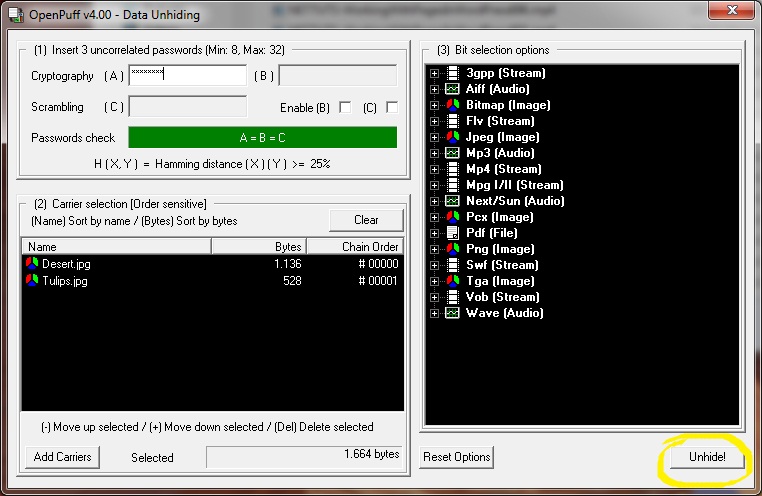
The two simplest ways to get your data back out of these files is to either change the extension from .mp3 to .zip or to open your chosen ZIP program and open newfile.mp3 within that. You should now be presented with your original files.
One more way of getting your .zip file back is to run this code:
This is clearly not a secure way to store your data but as a quick and dirt solution to hide files it works well enough. If you are storing text documents in the ZIP then the contents of them will still be visible in a HEX editor looking at newfile.mp3. There are much better steganography tools that use encryption keys to securely store your data within other files.
This method only appends new data (from secret.zip, in this article) into after the footer identifier of mask file (sound.mp3). Good media player will only read from header to footer, and will not read further than that. So whatever data we add will not be read, and the original file will remain in good condition. only it’s size is changing because we add more data into it. The same applies to every file which has header and footer identifier (e.g. jpeg, png, gif, mp3, mp4, exe, and most of known file format).